Risk information map for an industrial construction site. Why do you need a company risk map and how to draw it up. Risk map and operational planning
In the course of identifying and assessing financial risks, various graphical methods are used that provide a visual representation of the distribution of risks in time, by type of activity, by stages of a business process, in space (for example, by premises), by the amount of identified damage, etc. But the most universal information visualization tool, widely used in risk management, is the so-called risk map. It is built on the basis of a register of risks and their qualitative and quantitative characteristics obtained during the measurement process. A risk map can be built either for the entire organization or for any department. In addition, risk maps can be drawn up for the direction of the organization’s activities or for a separate project or program.
The simplest risk maps are usually presented in tabular form. In cases where qualitative and quantitative scales of probabilities and consequences are used to measure risks, matrix risk maps are used. Matrix risk map is a graphical and textual description of a limited number of risks of an organization, located in a rectangular table, on one “axis” of which the strength of impact or significance of the risk is indicated, and on the other, the probability or frequency of its occurrence. In cases where qualitative and quantitative scales of probabilities and consequences are used to measure risks, the entire range of risks is divided into cells. Due to its external similarity, such a risk map is sometimes called a “matrix”.
Generally speaking, the methodologies for constructing a risk map are as different as the risks of companies are different. The construction of a risk map can be carried out both as part of the implementation of a risk management system at the level of the entire organization, and to solve a separate range of risk management tasks. Methods that consultants (experts) use when drawing up a risk map include interview , formalized And informal questionnaires for reviews And industry research , analysis of the company's documentation set and numerical assessment methods and so on.
The composition of the team of consultants (experts) is very important for the success of the risk mapping process. When carrying out work by professional consultants, the team (working group) usually includes those specialists who have experience and expert knowledge. Experience shows that a team works effectively if it consists of six to ten people. Only by defining the boundaries of the analysis can you determine who is included in the team. When drawing up a map of the company’s financial risks, the team must include the head of the financial department, the head of the legal, control, GG departments, etc. The degree of detail required in the analysis is specific to each risk and varies from one risk to another, but depends mainly from the goals pursued by the organization.
Mapping is a complex process that involves many specific activities, but in general terms it involves visualizing identified risks. Risk identification includes financial risk analysis aimed at identification and assessment of risks.
Let us recall that identification is the first and one of the main stages of risk analysis. The results of risk identification make it possible to describe and compile a risk register. Risk assessment involves determining (calculating) the main qualitative and quantitative parameters (magnitude) of risk.
The results of risk identification and assessment are entered into financial risk maps. To build a financial risk map (hereinafter referred to as the Map), you must complete the following sequential steps and fill in all the columns of the following table (Table 2.6).
On initial stage identification presupposes choice of risk owner (risk subject). In our Map this is the line - job title.
The so-called risk owners (from English - riskowners) – These are employees, specialists whom the manager instructs to monitor the triggers of some specific risk, as well as manage response procedures in the event of this risk occurring. Employees become risk owners because of specific expertise regarding a particular issue or because they have some control over a specific risk.
Here the employee’s position is selected and the types of activities he performs and the management objects associated with these activities are identified. We will enter the selected type of activity in column 2 Maps.
The group of subjects with increased financial risk includes those that are characterized by:
- the presence of powers related to the distribution of significant financial resources;
- a high degree of freedom of action caused by the specifics of their work;
- high intensity of contacts with organizations and their representatives.
The next step is to define a list job responsibilities with high financial risk. Identification and assessment of risks is carried out according to a specific list of job responsibilities with a high probability of financial risks.
Column 3 Cards involves consideration and analysis of work conditions. Usually the following conditions are distinguished:
FINANCIAL RISK MAP No.________________
Department: _________________________________________________
Job title: ____________________________________________________
Filled out
(Head of unit) (signature) (Last name I. O.) (date) AGREED
Head of organization (division) ____________________________________________________________
______________________________________________________________________
- (EXPERT/CONSULTANT)
- normal (planned activities) – designated by the letter “N”;
- emergency (incidents and other emergencies) – designated by the letter “A”.
Identification of specific types of financial risks associated with selected activities is recorded in column 4 Maps.
The identified risks are described and documented in the form of a Register of Financial Risks (Table 2.7).
Table 2.7
Register of financial risks
|
Object of risk |
Risk name |
Description of the risk |
Risk factor |
|
|
P |
Count 5 Cards involves the identification of existing measures against the impact of hazards (regulations, measures) for the selected type of activity (work). Measures against exposure to hazards include:
- training and advanced training in the field of minimizing financial risks;
- carrying out certification of workplaces;
- carrying out certification of workplaces according to working conditions;
- testing of implemented standards, norms, regulations;
- identifying areas of business processes not covered by controls;
- identifying ineffective controls;
- introduction of new indicators of financial risks;
- other similar measures.
Identification of incidents (commercial bribery, official forgery, trading of insider information, abuse of authority, etc.) in the organization is filled out in column 6 Maps. Information on incidents is accumulated in the table presented (Table 2.8).
Table 2.8
Information on incidents
Description of the severity of the hazardous event (assumed - in the absence of statistics) from the possible impact of the hazard (column 7 Cards) taking into account the implementation of existing measures against this impact (standards for minimizing financial risks).
The most difficult step is assessing the risk. The risk assessment associated with the identified hazard is recorded in columns 7–10 Maps.
The risk associated with an identified hazard is assessed using the following formula:
where P is risk; T – severity of harm; – probability of danger occurrence; – exposure to hazards.
The severity of harm (T) is estimated at point system(for example, in ten-point scale) and filled out in the form of a table (Table 2.9).
Table 2.9
Severity of harm T
|
Characteristic |
|
|
Bankruptcy |
|
|
Loss of primary financial document |
The severity of harm is determined by the expert assessment of the working group that conducts the mapping. They determine the severity and assign points based on the specifics of the business entity. Therefore, for example, the harm from the revocation of a license to carry out transactions in foreign currency for some organizations will be 9 points, and for others, non-core organizations, much less.
The probability of harm (B) is considered by experts in terms of the likelihood of the hazard occurring and exposure to the hazard and is filled out in the following tabular form (Table 2.10).
Table 2.10
Probability of harm B
|
Probability of occurrence of danger, B1 |
Exposure to hazard, B2 |
|
|
1 event per day |
From 90% of working time |
|
|
1 event per month or less |
80 to 90% of working time |
|
|
1 event per quarter |
70 to 80% of working time |
|
|
1 event per half year |
60 to 70% of working time |
|
|
1 event in 9 months |
50 to 60% of working time |
|
|
1 event in 1 year |
40 to 50% of working time |
|
|
1 event in 2 years |
30 to 40% of working time |
|
|
1 event in 3 years |
From 20 to 30% of working time |
|
|
1 event in 4 years |
From 10 to 20% of working time |
|
|
1 event in 5 years |
Up to 10% of working time |
Further, the identified risks must be sort. Let's look at the real sorting technique large quantity risks, which has proven itself in hundreds of companies. It is actively used and promoted by the Risk Management Special Interest Group ( RMSIG ) from Project Management Institute. The essence of the method is to distribute risks over a special card (its other name is PI- matrix). The map should look as shown in the table. 2.11. Typically, all identified risks are distributed among the risk team members. As a rule, the one who identified the risk is responsible for the risk (source indicated at RMC- map). Risks identified by those not present for the procedure are shared equally among all other participants. Then the participants distribute their risks into certain squares, i.e. rank the probabilities and degrees of impact of these risks.
Table 2.11
Risk sorting map
|
Probability |
||||||||
|
Impact level |
||||||||
It may be necessary to improve the quality of individual decisions about the likelihood and impact of risks. It is recommended to distribute markers of different colors to team members and ask them, after reviewing all the risks, to mark those with which they do not agree and which, in their opinion, need to be discussed separately. The flagged risks are then discussed and appropriate changes made. At the end of this step, the likelihood and degree of impact of each risk on the project is considered established, and RMC- cards, the probability of a given risk and the degree of influence are entered.
In addition to the risk sorting procedure, they must be propagate those. define R.R. (from English - risk ranking) for each risk. Formula for determining R.R. is this:
R.R. = Probability of risk (IN) × Risk exposure ( Y ).
This step repeats the sorting of risks on the map, but experts advise carrying it out, since it will be needed in the future. Then you can determine which risks will be included in the risk management process. List of risks according to value R.R. allows you to sort them. In this way, risks that have a very low probability of occurring or will have a very small impact on the project can be removed from further analysis.
The most important thing at this step is to decide on the threshold values of risks that will be included in further consideration. This is a complex issue on which it is difficult to give specific recommendations. The experience of the project manager plays a huge role here, as well as the risk levels that are accepted as thresholds in the company. If the company has adopted a maximum project risk level of 70, then all risks that have R.R. above 45–50 should be considered significant. All risks that have R.R. below 45–50, are documented, but are not put into risk management work. The identified risks are ranked, their written description is compiled, which is entered into a special table (Table 2.12). A similar table is filled in by each expert.
Table 2.12
Risk ranking map
|
Object of risk |
Risk name |
Risk factor |
Probability of occurrence |
Damage from risk |
Risk index (I r = B × Y) |
|
|
P |
The results of risk identification and assessment are entered into Maps for presentation to management. The identified, sorted and ranked risks are entered into the first version of the final Corruption Risk Map. In fact, we have already done part of this work by filling out the table. 2.6.
For a more visual representation, the identified and sorted risks are entered into a matrix Risk Map. Depending on the degree of danger, several categories of risks are distinguished. The number of categories corresponds to the needs of the study. You can use the table below as a starting point. 2.13. It will help determine High , Average or Low risk depending on its likelihood and consequences. For example, the combination High probability + High influence will obviously mean High level risk.
Table 2.13
Risk level
|
Severity of Consequences/Probability of Occurrence |
Overall risk level |
|
High Losses/High Probability |
|
|
High Loss/Medium Probability |
|
|
High Loss/Low Probability |
Medium/Low |
|
Medium Loss/High Probability |
|
|
Average loss/Average probability |
Medium/Low |
|
Medium Loss/Low Probability |
|
|
Low Loss/High Probability |
|
|
Low Loss/Medium Probability |
|
|
Small losses/Low probability |
These nine simple combinations of risk characteristics can also be presented in tabular form as follows (Table 2.14).
Table 2.14
Level of risk and measures to manage it
|
Likelihood/Impact |
|||
The cells represent combinations of probabilities and consequences that can be safely ignored. The cells represent combinations that require urgent risk management measures. The cells represent combinations that require close attention and regular re-evaluation in the future.
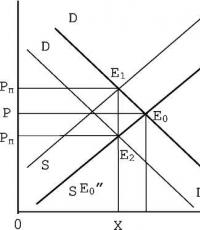
The risk assessment is valid for a certain period. To have grounds to apply the apparatus of probability theory, this period must be quite long (three to five years). If the probability of an event (for example, theft) is low, the period under consideration should be further increased. But during this time the situation will change significantly and the old estimates will lose meaning. Consequently, when assessing risks, events with a probability less than a certain threshold value can be neglected, despite the fact that the potential damage from them may be great. Note that this is contrary to traditional practice, when managers tend to pay excessive attention to risks with high damage and low probability. In fact, in the foreground there should be risks with moderate damage, but a high probability (for example, malicious attacks software), which are implemented many times during the period under review. At the same time, it must be borne in mind that the probability of a negative event is very difficult to assess with any accuracy. Therefore, it is recommended to consider risks not as numerical values, but as points on a plane, where the coordinate axes are probabilities and losses (Fig. 2.4). The level lines for the risk function are hyperbolas.
Event risk U1 is one of those usually overestimated by managers; in practice, due to the low probability, it is advisable to neglect most of such risks.
Very important step in risk analysis is to determine the limit of risk tolerance. Risk tolerance limit – critical limit of risk tolerance. The choice of tolerance line is made by a strong-willed decision of the company’s management. Financial risks located above and to the right of the boundary are considered “unacceptable” and require immediate management attention. Those threats located below and to the left of the border are currently considered tolerable.

Rice. 2.4.
by us. The risk tolerance limit changes depending on the organization's risk appetite. When classifying risks by significance/probability, even without a numerical assessment, you can roughly estimate the amount of financial losses from a particular risk, which allows you to determine to some extent the organization’s appetite for risk and determine the limit of risk tolerance on the map. In order to visually represent the limits of risk tolerance (tolerance, acceptability), the financial risk map is presented in the following form (Fig. 2.5).

Rice. 2.5.
Risk acceptability limits allow you to immediately visually determine the division of risks into categories in terms of the danger they pose. The risk map can be a little more complicated and presented in color. For example, a matrix Risk Map may look like this (Fig. 2.6).

Rice. 2.6.
This risk map displays probability or frequency on the vertical axis and impact or significance on the horizontal axis. In this case, the probability of risk occurrence increases from bottom to top as you move along the vertical axis, and the impact of risk increases from left to right along the horizontal axis. The Arabic numerals on the map are designations of risks that have been classified so that each probability/significance combination is assigned one type of risk.
This classification, placing each risk in a specific separate “box,” is not mandatory, but simplifies the process of setting priorities by showing the position of each risk relative to others (increases the resolution of this method). The thick broken line is the critical limit of risk tolerance; cells are combinations of probability and significance (consequences) that can be completely safely ignored. When identifying critical risks, scenarios leading to risks above this limit are considered unacceptable.
They are marked on the map and . The cells represent combinations that require close attention and regular re-evaluation in the future. Based on identified unacceptable (intolerable) risks, it is necessary to understand how to reduce or transfer such risks, while risks below the border are manageable in an operational manner. Risk management corresponds to the movement of points along the plane. Usually they try to approach the origin of coordinates along one axis without changing the value of the other coordinate. However, if you can reduce both coordinates at once, it will be even better. In fact, depending on the building goals, you can build many different types risk maps or variations of a given risk map.
The register and risk maps compiled on its basis are the main information base to make decisions on further risk treatment. For the most accurate risk assessment possible, it is essential to take into account the full group of factors that determine risk. The set of risk factors must reflect all conditions of the organization’s external and internal environment that give rise to possible corruption risks.
The risk map has been drawn up; now it is necessary to develop measures to neutralize those risks that turned out to be above the tolerance limit. Based on the Maps of divisions, experts (consultants), together with interested divisions and specialists of the organization, within 10 working days, draw up a “Register of unacceptable risks of the organization (division)”. The working group should determine whether to leave everything as is and take no additional actions or develop new plan risk management actions if you are not satisfied with their consequences. As a result of the activities carried out, it is possible reduce the likelihood of risk , reduce the likelihood of losses , or change the consequences of the risk.
The goal of creating an action plan is to figure out how to move each intolerable risk further to the left - lower into the tolerable zone. It should be noted that it is necessary to weigh the costs of such a move against the benefits of it. Proposed controls for unacceptable risks must first be assessed for the presence of new hazards and associated risks. The degree to which a risk is acceptable depends on the importance to each risk subject and their goals and expectations. The method of influencing the risk is selected. For example, if a risk has been determined to be unacceptable, then a mitigation option is developed. If it does not reduce the risk level to an acceptable level, then the avoidance option is used. If it is impossible to transfer the risk, it must be accepted with the obligatory reservation of funds in case of unforeseen circumstances.
From the point of view of risk management technology, with the construction of a risk map, the management process does not end, but only begins. Moreover, a risk map is a “living organism” that reacts to decisions made and operations performed. It lives and develops with the development of the organization; along with new opportunities, new risks appear; some of the old risks lose their relevance and become insignificant and insignificant for the organization. Therefore, it is important that the process of mapping risk and clarifying the map is built into the actions of the organization. This will allow the organization’s risks to be updated as often as necessary. Typically, the period for “planned updating” is a year; sometimes it is tied to certain cycles (seasonal, calendar) if they occur in the organization’s activities. However, when even weak signals about events that can greatly affect the organization’s risk objects, their impact on the organization’s risk map should be assessed without any frequency. It is important to understand that the value of a risk map lies not in determining the exact size of the probability or damage of risks, but in the relative location of one threat to another and their location relative to the acceptability boundary.
Thus, risk mapping is a universal analytical tool for understanding the financial risks of business entities, ranking them by importance, and preparing measures to minimize them.
- URL: iemag.ru/master-class/detail.php?ID=15716
In a simplified way, management technology in the concept of acceptable risk is perceived as a sequence of three large stages of identification, assessment and minimization. Let’s assume that during the implementation of the first stage, management formulated goals and set tasks for the company’s risk management. The next step is to identify and identify the main threats to current and future activities. One of the effective and visual tools for such work is a risk map.
Risk mapping stage
Independent fight against risks in business, as a rule, begins with a traditional SWOT analysis and description of threats. This includes the analysis of documentation: regulatory, financial, managerial, marketing, contractual. Current policies, regulations, and the results of sessional strategic activities are examined. In the course of research and collegial work, a composition of external and internal factors that can influence the level of risks is formed.
As a result, the identified threats are subject to compilation into a single table, which is a system of risk factors with a list of them, sometimes called a risk factor profile. In addition to the summary table, it is also advisable to develop a classification scheme of factors with highlighted relationships between them. A more specific form of identifying factors is their identification. Identification of risks involves identifying their most significant qualitative and quantitative characteristics, which include:
- likelihood of manifestation;
- the extent of potential damage;
- place of origin;
- level of relationships between factors, etc.
In other words, the risk must be compared with the specified parameters. At the moment when we begin to comprehend the extent of the damage, a transition occurs to the second stage of management technology - the assessment stage. Risk measurement within the framework of factor identification and initial assessment is carried out instrumentally, first qualitatively and then quantitatively.
The second measurement tool is mapping. When we first start working with factors, we strive to describe them at the level of: likely - not likely, dangerous - not dangerous and how dangerous. On this basis, it is possible to construct a map with the abscissa axes, on which the danger scale is built, and the ordinate axes, with the placement of the risk probability scale on it. Factors are reflected on the created field and receive visual positioning on it.

Risk map model
Each company itself establishes the concept of danger and its units of measurement. For the managers of one company, this means lost profit; for others, it means income. For example, we can assume that the danger within the loss of profit up to 33% is not dangerous, in the range from 33% to 67% the danger is acceptable, and above 67% is no longer acceptable. Some authors believe that a factor can be dangerous if it can lead to a complete loss of profit (100%). The probability range from 0 to 1 is divided into three or more groups, suppose:
- from 0 to 0.2 – unlikely;
- from 0.21 to 0.65 – probable;
- over 0.65 – very likely.
The above example of partitioning ranges is not a dogma; in each specific case the approach is individual. Next, responsible employees, taking the data from the completed table of risk factors (the form is located below), transfer each factor to the risk map, taking into account probability and danger. Depending on the sector of the matrix in which the factors fall, you can see on the map which risk zone they belong to.

Table of the system of factors influencing the level of risk
Risk map analysis
It is recommended to build or correct the map once a quarter. Each time after such work an analysis should be carried out. It allows you to cut off a group of risks that are dangerous (above the red line drawn on the map). In addition, non-hazardous risks that fall in the quadrants below the blue dashed line become obvious. The risk map during the analysis makes it possible to draw the following conclusions.
- For the risk group above the red line, an immediate (priority) action plan should be developed.
- For the group of risks included in the zone between the red and blue lines, the development of an annual action plan is required.
- For risks located below the blue line, it is necessary to create a plan of controlled measures so that over time they do not become acceptable or even dangerous.

Example of a visual form of a risk map
Above is an example of a different map view. The probability values of the factor are indicated inside the circles. At the very top of the map we see two risks that can confidently be called key. Key risks should be understood as threats that can cause irreparable, catastrophic damage to a business. This type of damage includes stopping continuous production in conditions of risks of man-made disasters, for example, in metallurgy, or even the loss of the business itself with the threat of the emergence of so-called “killer technologies”.
Risk maps can be generated not only in graphical, but also in tabular form. Below is an example of such a map. Risk factors are placed along the rows, and probability and danger scales are sequentially placed in the columns. The table is filled out by putting “+” in the cells corresponding to the risk factors for the two main assessment parameters. The zone of the most dangerous risks includes factors that have a mark in every third column. In our example, this is “increasing production costs.” Controlled risks, on the contrary, have marks in each first column. In the example, these include “inventory growth” and “staff turnover.”

Example of a risk map in tabular form
When constructing a risk map, a reasonable question arises: “Could we be wrong?” Certainly! The mistake may lie in the selection of experts. And the experts themselves are capable of making mistakes, unfolding the situation in a subjective assessment of factors. But by regularly assessing and bringing the results into the focus of their attention, decision makers learn time after time to identify long-standing problems and find new threats. In addition, the skill of correctly setting priorities and timely minimizing risks is being developed. In any case, the present tool is effective in its own right.
Identification of hazards in the workplace is carried out with the aim of identifying and clearly describing all hazards for all types of activities of the organization, including planned and unscheduled activities, for further risk assessment and management and should take into account:
situations, events, combinations of circumstances that led or could potentially lead to injury or occupational disease employee;
causes of potential injury or illness related to the work, product or service performed;
information about past injuries and occupational diseases.
It is necessary to evaluate both normal working conditions and cases of deviations in work associated with incidents and possible emergency situations.
When identifying hazards depending on the type of activity being carried out, it is necessary to determine list of works included in the type of activity being carried out, and also consider not only the hazards and risks from the activities performed by its personnel, but also the hazards and risks arising from the activities of contractors and visitors, from the use of products and services provided by other organizations.
This procedure includes consideration:
organization of work, including the safety of its execution;
designing safe workplaces, technological processes, equipment;
installation, operation, Maintenance, repair of equipment (buildings and premises);
characteristics of goods and services purchased by the organization.
Responsibility and authority.
The functions performed and responsibilities for identifying risks associated with the activities of the enterprise and assessing their significance are given in the matrix of distribution of responsibilities (Appendix 1).
Description of activity.
General provisions.
In order to effectively manage the activities of the enterprise and individual departments in the field of occupational safety, the enterprise has established procedures for identifying hazards and assessing risks.
Hazard Identification
When carrying out hazard identification, the following were studied: Required documents on labor protection:
Records of all types of condition monitoring labor protection(logs of daily, monthly monitoring of the state of labor protection, inspection reports);
Results of surveys and inspections of labor protection by state supervision and control bodies, occupational safety and health;
Statistics of microtraumas, accidents, accidents and incidents at the enterprise;
List of works with increased danger;
Records on training, briefing and testing of workers’ knowledge;
Labor protection instructions, etc.
Hazards that create risks of potential harm to the life or health of an employee, damage to the property of the enterprise, disruption of the environment at the workplace, or a combination of these when performing work are indicated in the classifier (Appendix 7).
Risk classification.
The enterprise's OSMS establishes the following classification of risks by level of significance:
|
Acceptable risks |
low |
|
average |
|
|
Unacceptable risks |
high |
|
very high |
TO low risks(R<6) относятся потенциальные риски при ежедневной работе на рабочем месте. Риски с таким уровнем рассматриваются как приемлемые при наличии мер по управлению ими (инструктаж по ОТ).
TO medium risks(P=6-12) include risks in which there is a potential threat to the health of personnel and/or damage to the organization’s property. Risks with this level are considered acceptable if there are sufficient measures to manage them and require constant monitoring and analysis.
TO high risks(P=14-25) include risks in which there is a potential threat to the life and health of personnel and/or causing significant damage to the organization’s property. Risks with this level are considered unacceptable and require further mandatory management.
TO Very high risks(P=27-45) include risks in which there is a real threat to the life and health of personnel and/or significant damage to the organization’s property. Risks with this level are considered unacceptable and require mandatory management.
Risk assessment.
Risk assessment in the organization is carried out using the calculation method in accordance with the methodology given in Appendix 3 for professions and positions specified in Appendix 4.
Risk value assessment cards (Appendix 5) are filled out by the heads of structural divisions for each division of the organization and agreed with the head of the OSH bureau, with the obligatory reflection in them:
professions;
descriptions of the hazard;
residual risk assessment ( P);
The card is used in departments for:
assessing the state of occupational safety in the department for the year;
preparation of input data when conducting an analysis of the occupational safety and health system by the management of the enterprise;
assessing the effectiveness of corrective and preventive actions taken to reduce the level of risks for a given profession.
Risk assessments in completed cards are made in relation to hazards identified from work practices.
Heads of structural units enter unacceptable risks into the register of unacceptable risks of the structural unit (Appendix 5) and transfer a copy of the register to the OTO.
The head of the safety bureau, based on the registers of unacceptable risks of structural divisions, compiles a register of unacceptable risks of the organization (Appendix 7) and submits it to the chief engineer for review and approval.
For low risks, the development of corrective actions (measures) is not required.
For unacceptable risks, it is mandatory that the heads of the structural divisions of the enterprise develop measures to manage them, which are agreed upon with the chief engineer and approved by the director of the enterprise.
These activities may be related to:
Production equipment;
Staff awareness and training;
Procedures to ensure the safe operation of equipment, emergency response, accident prevention, etc.
After completing the developed measures, a re-assessment of risks is carried out and an analysis of the effectiveness of risk management measures is carried out with further inclusion of the expected risk reduction in the risk assessment card (residual risk assessment ( P, S, R), filled out by heads of structural divisions.
Analysis and management of the hazard identification and risk assessment process.
Every year, before holding a meeting on the analysis of the occupational safety and health system by management, the heads of structural units, in order to assess the effectiveness of risk management measures taken and set new goals in the field of occupational safety and health, carry out hazard identification and risk assessment for their structural unit, filling out Risk Assessment Cards and Registers of Unacceptable Risks.
Heads of structural units also ensure unscheduled hazard identification and risk assessment within a month in the following cases:
Introduction of new regulatory legal acts and technical regulatory legal acts in the field of occupational safety;
Expansion, reduction, change in the structure of the unit;
Redistribution of responsibility;
Changes in operating methods and modes;
Introduction of new technologies and equipment.
Information on the use and storage of documents containing registered data (records) based on the results of work established by this standard is given in Table 1.
Table 1
|
Name document |
Storage location of the original (copy) document |
Term storage document |
|
Cards for assessing the risk value for the profession | ||
|
Register of unacceptable risks of structural divisions |
Structural unit (BOT) | |
|
Register of unacceptable risks of the enterprise | ||
|
Hazard classifier |
BOT (structural unit) |
The safety specialist is responsible for updating and making changes. The director of the enterprise approves the changes.
Accounted and registered copies of this standard or amendments to it after the issuance of the director’s order to put it into effect are distributed.
I APPROVED
Director
"___" __________ 2011
Put into effect:
Order No. _______ dated ________
Organization standard
Environmental Management System
STO OHSAS 23-2011
HAZARD IDENTIFICATION,
RISK ASSESSMENT AND DETERMINATION OF CONTROL MEASURES
1. Purpose | |
2. Scope of application | |
4. Terms and definitions | |
5. Abbreviations | |
6. Responsibility | |
7. Description of the procedure | |
7.1 General provisions | |
7.2 Hazard identification and risk assessment procedures | |
8. Documentation | |
Annex 1 Form for recording hazardous and harmful production factors | |
Appendix 2 Risk assessment methodology | |
Appendix 3 Hazard Identification and Risk Assessment Card Form | |
Appendix 4 Significant Risk Register Form | |
Approval sheet……………………………………………………….. | |
Change registration sheet……………………………………………………………… |
1 PURPOSE
This organization standard establishes the procedure for identifying hazards in the field of health and safety associated with the activities of the organization, assessing and analyzing risks, as well as managing them.
2 AREA OF APPLICATION
The requirements of this organization standard apply to all types of work activities of the organization’s employees, as well as to the activities of contractors, visitors and suppliers.
This organization standard is mandatory for use by all officials and structural divisions of the organization.
3 NORMATIVE REFERENCES
This organization standard uses references to the following documents:
(Cite documents to which references are given in the text of your standard)
4 TERMS AND DEFINITIONS
This organization standard uses the following terms with appropriate definitions:
Acceptable risk – a risk that has been reduced to a level that the organization can support, taking into account its legal obligations and the obligations of its own health and safety policy.
Significant risk– the risk that the organization undertakes to manage.
Hazard identification– the process of recognizing that a hazard exists and determining its characteristics.
Danger - a source or situation of potential harm in the form of injury or illness, property damage, damage to the environment surrounding the workplace, or a combination thereof.
Risk assessment– the general process of determining the magnitude of the risk and deciding whether the risk is acceptable or not.
Risk– a combination of the probability and consequence(s) of the occurrence of a specific hazardous event.
Risk management– reducing (maintaining at a certain level) the magnitude of risk through various measures.
5 ABBREVIATIONS
The following abbreviations are used in this standard:
OH&S – occupational health and safety management system.
6 RESPONSIBILITY
6.1. Management representative (chief engineer):
Provides organization of work to identify hazards in the field of occupational safety of the enterprise, assess the risks associated with them and manage them;
Approves the register of significant risks of the organization.
Provides methodological assistance to structural units in identifying hazards and assessing risks;
Develops and updates a register of significant risks of the organization.
6.3. Heads of structural divisions:
Ensure the organization of work to identify hazards, assess risks and manage them in their structural units;
Develop and update hazard identification and risk assessment maps.
7 DESCRIPTION OF THE PROCEDURE
7.1 General provisions
7.1.1 Hazard identification Risk assessment is carried out to determine the significant impacts of the organization's production activities on the health of workers and occupational safety.
7.1.2 Hazard identification, risk assessment and subsequent risk management activities are carried out in the organization as an ongoing process that determines the past, current state and potential impact of the organization’s activities on employee health and occupational safety.
7.1.3 Initially, hazards are determined based on the results of a preliminary analysis of the state of health and safety.
The preliminary analysis considers:
Legislative and other requirements;
Results of investigations of accidents, accidents and incidents.
7.1.4 When identifying hazards, direct and indirect hazards are determined.
Direct dangers are associated with:
Personnel of the organization;
Production equipment;
Materials and substances used in the production process;
Technological features of production processes;
The state of the production environment;
Unreliable means of employee protection;
Reduced level of safety of production means due to their wear and tear during operation.
Indirect dangers are associated with:
Activities of contractors, suppliers;
Visitors.
7.2 Pprocedure for hazard identification and risk assessment
7.2.1. In structural divisions, all work on hazard identification and risk assessment is organized by the heads of structural divisions.
7.2.2. Heads of structural divisions determine dangerous and harmful production factors at the workplaces of the structural division in accordance with Appendix 1 and submit the completed forms to the occupational safety and health manager to compile a list of the organization’s hazards. The list of hazards is approved by a management representative.
Heads of structural divisions carry out:
Identification of hazards associated with the selected activity or process;
Assessing the risks from identified hazards using a risk assessment methodology.
In this case, risks are considered in the following situations:
Normal working conditions;
Abnormal operating conditions (starting and stopping equipment, unintentional and possible (predictable) incorrect use of equipment, material, process, potentially emergency or emergency situations, etc.)
The risk assessment methodology is given in Appendix 2. Moderate and significant risks are classified as significant.
Development of risk management measures, if the risk is significant, and repeated assessment of it in order to determine the value of the residual risk.
If there are residual risks that are significant, special measures are required to manage such risks (inclusion of an activity or process in the list of work with increased danger; performing work under a work permit; undergoing special training; strengthening control over the performance of work, etc.)
Significant risks are given special attention, since measures to manage (maintain at a certain level) such risks are taken into account when setting goals in the field of health and safety and are included in the OSH program.
Filling out hazard identification and risk assessment cards. The form of the hazard identification and risk assessment card is given in Appendix 3.
Hazard identification and risk assessment cards compiled in structural units are transferred to the occupational safety and health manager.
7.2.3. The occupational safety manager, after analyzing hazard identification cards and risk assessments, compiles a register of significant risks of the organization, which is approved by a representative of management.
The form of the register of significant risks of the organization is given in Appendix 4.
7.2.4. Based on the register of significant risks, the occupational safety manager determines the activities that need to be included in the health and safety management program.
7.2.5. Hazard identification and risk assessment cards are updated by heads of structural divisions once at the end of the calendar year or as needed. Copies of updated hazard identification and risk assessment cards are transferred to the occupational safety manager to update the organization’s register of significant risks.
7.2.6. The basis for revising hazard identification and risk assessment maps are:
Changing the composition of the organization's personnel;
Changes in legislation in the field of health and safety;
Purchase of new materials, including hazardous ones;
Changing the technological process;
Results of the analysis of accidents, occupational diseases, incidents, inconsistencies;
Occurrence of emergency situations;
Analysis of internal audit results;
Management analysis.
8 DOCUMENTATION
Name document | Executor (job title, structural subdivision) |
storage control copy | Shelf life |
List of organizational hazards | Heads of structural divisions, labor protection manager | Labor Safety Manager | Before replacing with new ones |
Hazard identification and risk assessment cards for structural units | Heads of structural divisions | Structural units | |
Register of significant risks of the organization | Labor Safety Manager | Labor Safety Manager |
APPLICATION1
Form for recording hazardous and harmful production factors in the workplace
Structural subdivision _______________________________
Dangerous and harmful production factors in accordance with the classification according to GOST 12.0.003-74 | Workplace or profession |
|||||||
Physical hazardous and harmful production factors |
||||||||
moving machines and mechanisms; | ||||||||
moving parts of production equipment; | ||||||||
moving products, workpieces, materials; | ||||||||
increased dust and gas contamination of the air in the working area; | ||||||||
increased or decreased temperature of the surfaces of equipment and materials; | ||||||||
increased or decreased air temperature in the working area; | ||||||||
increased noise level in the workplace; | ||||||||
increased level of vibration; | ||||||||
increased level of infrasonic vibrations; | ||||||||
increased level of ultrasound; | ||||||||
increased or decreased air mobility; | ||||||||
increased voltage in an electrical circuit, the closure of which can occur through the human body; | ||||||||
lack or lack of natural light; | ||||||||
insufficient illumination of the work area; | ||||||||
sharp edges, burrs and roughness on the surfaces of workpieces, tools and equipment; | ||||||||
location of the workplace at a significant height relative to the surface of the earth (floor); | ||||||||
Chemical hazards and harmful production factors |
||||||||
Psychophysiological hazardous and harmful production factors |
||||||||
physical overload; | ||||||||
neuropsychic overload. | ||||||||
others (specify which ones) |
Head of department ____________ _______ ________
This mini guide, using a practical example, presents the stages of hazard identification and risk assessment in a manufacturing plant in accordance with the requirements GOST 12.0.230-2007 (OHSAS 18001:2007) . The presented practical guide reveals the main idea of the standards for the occupational safety and health management system GOST 12.0.230-2007 (OHSAS 18001:2007), aimed at improving the occupational safety management system at the enterprise, reducing unforeseen costs (for the elimination of accidents, incidents, insurance payments, etc.) .d.), increasing labor productivity, as well as increasing the loyalty of staff and society.
Introduction
1. The concept of danger and risk
2. Stages of work on hazard identification and risk assessment
3 Risk management in emergency situations
4 Development of measures to improve the occupational safety and health management system
Conclusion
Introduction
 According to the Federal Labor Inspectorate of the Russian Federation, currently in Russia more than 600 people die every month at work, 1000 people become disabled, about 20% of people work in conditions that do not meet sanitary and hygienic standards. The share of jobs with harmful and dangerous working conditions has increased from 1995 to the present by more than 5% and in recent years has averaged approximately 23%, reaching a third and even a half in certain industries. Primary disability claims have increased by approximately 50% since 1995.
According to the Federal Labor Inspectorate of the Russian Federation, currently in Russia more than 600 people die every month at work, 1000 people become disabled, about 20% of people work in conditions that do not meet sanitary and hygienic standards. The share of jobs with harmful and dangerous working conditions has increased from 1995 to the present by more than 5% and in recent years has averaged approximately 23%, reaching a third and even a half in certain industries. Primary disability claims have increased by approximately 50% since 1995.
Taking into account the real volume of production, injury rates in Russia are constantly increasing (with some numerical reduction in the number of injuries at work in recent years). Economic losses in this case increase annually by 10-30%.
From foreign experience we note the following.
According to international standards, the employer is obliged to insure each employee not only against accidents at work, but also against damage associated with treatment.
The International Labor Organization recommends the minimum amount of such insurance to be 7,500 working days' salary.
In countries with a strong trade union movement, collective agreements include the employer's obligation to insure its workers also against the consequences of domestic injuries and general illness, sometimes together with family members.
In connection with accession to the WTO, Russian organizations will need to be guided by similar international standards in the field of occupational safety, and in order to avoid the above problems in the future, domestic companies will need to modernize their occupational safety management system.
Something is already being done now - for example, since January 1, 2010, changes have been made to the Labor Code of the Russian Federation regarding labor protection requirements. In the new version of the Labor Code of the Russian Federation, the requirements of occupational safety system standards are equated to occupational safety requirements, which includes more than 120 occupational safety system standards (OSSS), now equated to state ones and mandatory for use.
The presented manual reveals the main idea of one of the standards of the SSBT system - GOST 12.0.230-2007 (OHSAS 18001) - carrying out hazard identification and risk assessment occurrence of accidents and incidents. This work is very labor-intensive and costly, but for a Company that really cares about the health and safety of its employees, holding such events is simply necessary.
1. The concept of danger and risk
First, let’s define what “hazard” is and what “risk” is in the interpretation of the OHSAS 18001 standard (it is recommended to rely on it since GOST 12.0.230 does not yet fully comply with it).
Hazard is a source, situation, or action with potential harm in the form of injury or impairment, or a combination of these.
Risk is a combination of the likelihood of a hazardous event or exposure(s) occurring and the severity of the injury or impairment that may be caused by the event or exposure(s).
In order to understand these terms, we can give an example from everyday life. We encounter dangers every day - we travel in transport, cross the roadway, railway tracks and use electrical appliances - all this is a source of risk for deterioration of health. Those. in other words, DANGER is the source from which the risk of an accident comes. For example, even a car is regarded as a “highly dangerous vehicle” - i.e. a moving car is a danger, and a risk is already a potential dangerous event - i.e. An accident with a deterioration in a person’s health (injuries, fractures, or God forbid, death).
The biggest mistake of companies that start such work is confusion in terms. If initially the terms are misinterpreted, then it will be a “Sisyphean task”, because Without a common understanding of the terminology of the OHSAS 18001 standard, this system cannot be built. For example, the concept of “danger” is very often confused with the concept of “risk”. For example, the interpretation of the danger associated with a slippery floor - someone implies as a source - i.e. the source of risk is “slippery floor”, some - as the situation of “walking on a slippery floor”, others as an action - let’s say “washing the floors”. As a result, the risk of injury from falling on a slippery floor in practice can come from several sources (hazards), for example:
Because the floor was slippery;
Because they were walking on a slippery floor;
Because someone washed the floor.
Practice shows that it is more expedient to regard “danger” as a source of risk, and to regard the situation and action as a technological operation; therefore, the following scheme can be distinguished:

Thus, a common understanding of the terminology OHSAS 18001 by all employees involved in the development of an occupational safety and health management system is one of the key points in the effective implementation of OHSMS.
2 Stages of work on hazard identification and risk assessment
The work of identifying hazards and assessing risks can be divided into several stages (presented in a logical sequence, but some stages can and should be combined):
- Stage 1. Identification of the organization's activities
- Stage 2. Selection of individual technological operations
- Stage 3. Identification of hazards in process operations
- Stage 4. Risk identification
- Stage 5. Determining the level of risks and their ranking
- Stage 6. Development of risk management measures
- Stage 7. Allocation of responsibility for risk management measures
- Stage 8. Identification of legal and regulatory requirements for significant risks
Practice shows that for the effective implementation of this work, it is necessary to involve not only experts in the field of labor protection (OHS) (in an enterprise these can be OSH specialists and managers) but also heads of departments, since no one knows better than, say, the head of a workshop about all potential risks in his department.
Stage 1. Identification of the organization's activities.
At this stage, they are considered as standard activities of the organization, for example, such as production, warehousing, repair work, transportation of products, etc. (if the enterprise is large, then it can be divided into separate production processes), and non-standard activities that should also be taken into account when identifying hazards - design, activities of contractors, activities of nearby organizations, modernization, administrative and economic activities, etc.

For example, let's take a small factory producing plastic products. There is production with various technological processes, warehousing, transportation, repair work of production equipment, etc. (see Figure 1). If the enterprise has implemented a quality management system (QMS) according to the standard ISO 9001 , then the implementation of this stage is greatly simplified, since when implementing ISO 9001 the company's business processes are distinguished in relation to the following types of activities: main business processes (production, procurement, logistics, etc.), auxiliary processes (repair, maintenance, after-sales service, etc.) and management processes. Thus, the types of activities have already been highlighted in some form and you can continue to work with them. If there is no implemented QMS, then the types of activities can be distinguished according to the principle: main and auxiliary, standard and non-standard (for example, design or modernization).
At the end of the stage, we obtain a list of standard and non-standard activities, possibly broken down into more detailed areas (for example, in a furniture factory, the global furniture production process can be divided into the production of upholstered furniture and the production of cabinet furniture, and also if the technological chain is fundamentally different, then by types of production).
Stage 2 Selection of individual operations
Let's take the main type of activity, where, as a rule, the main dangers and risks are concentrated - production. In our case, the production of plastic products. In order to proceed to this stage, it is necessary to analyze the entire technological chain of manufacturing plastic products from the production of parts from raw materials to obtaining the finished product and break it down into separate technological operations (unless, of course, there is technological documentation where everything is described). Suppose, in our case, the production of plastic products consists of casting parts in an oven from granules, drying them, preparing them for assembly into a finished product (grinding, polishing), assembling the finished product by hot pressing, painting the product, varnishing, etc.
At the output of this stage, we obtain a list of technological operations (processes) for a specific type of activity (preferably in a logical sequence) tied to a specific activity. Such a list can be presented in the form of a table for clarity (Table 1).

It is imperative to include technologists and department heads in this work. After identifying technological operations in various types of enterprise activities, you can move on to the main 3rd stage.
Stage 3 Identification of hazards in technological operations
This is one of the most time-consuming stages. To qualitatively identify hazards, it is necessary to analyze a huge amount of information, namely:
- Analysis of documentation of the existing organization management system
- Analysis of legislative and regulatory documentation in the field of labor protection applicable to a given organization and in particular to individual technological processes and operations.
- Analysis of the current technical documentation of the enterprise (technological and work instructions, equipment operating instructions, situation plans, etc.)
- Analysis of records on registration of hazardous substances and materials (if any)
- Analysis of records on the investigation of accidents, incidents and breakdowns (including at similar enterprises);
- Analysis of records on monitoring and measurements in the field of labor protection (physical factors);
- Monitoring the implementation of “material” processes (production, logistics, etc.);
- Interviews with employees carrying out processes;
- Analysis of messages from stakeholders (Society, government), etc.
At the output of this stage, we obtain a list of hazards (risk sources) for each specific technological process (operation). To work more effectively at this stage, it is necessary to involve experts in the field of labor protection (including third parties) and heads of departments. The work of identifying hazards can also be broken down into separate steps depending on the size of the enterprise.
In the presented example, hazards from the technological operation “Assembling parts” are identified (the example does not show all possible hazards in this case, but only some of them). In our case, assembly is carried out using the hot pressing method, i.e. the operator works on a press, the surface of which, for example, has a high temperature. Based on the analysis of the above documentation by the working group and observation of the technological process, we identify those hazards that we will consider as a source of risk for a person, in this case the operator working on the press. Standard OHSAS 18001 also involves identifying hazards to equipment, and the risks of its breakdown and failure, but in this article we will talk about the dangers associated only with human health. We also enter the results of the work into the table (Table 2)

After the implementation of this stage, the first elements of the occupational safety and health management system are already visible - traceability of hazards to the types of activities of the enterprise appears.
4 Stage of identifying risks for each operation
At this stage, it is necessary to determine the potential deterioration in the health status of personnel from the identified hazards. Those. for example, we have a danger - high temperature of the surface of a press for assembling plastic parts - risks from such a danger can be, for example, the operator receiving a burn, heat stroke, or rapid fatigue from high temperature.
Information on risks can be obtained from regulatory documentation on labor protection (occupational safety system standards (OSS), work instructions, technological documentation, workplace certification records, accident and incident analysis records, etc.), as well as through expert assessment of employee performance (for example, observation of technological processes, inspections of workplaces, personal protective equipment, etc.). At this stage, it is necessary to involve not only internal occupational safety specialists, but also third-party expert organizations in this field, if possible.

Data on identified risks for each hazard are also entered into the table (Table 3) and we begin to assess the level of each risk.
Stage 5 Determining the level of risk and ranking them
After the titanic work of identifying hazards and risks has been done, we begin to rank the risks by significance. To do this, it is necessary to develop a methodology for determining the “significance” of risks. There is no single methodology for risk assessment and it is developed individually, being the “know-how” of each enterprise. This could be an expert risk assessment - where the risk level is determined by experts (a group of specialists) for each risk, and the introduction of a scoring system for the risk level. An expert assessment of the risk level is the most informative and reliable, but it is difficult to apply to large enterprises, as it is associated with large labor costs. Therefore, we will focus on a more universal score. The most common risk assessment formula is:

where P is the risk level,
S t – degree of risk severity (severity of consequences of the occurrence of a dangerous event),
H – frequency of risk occurrence.
In order to obtain a quantitative assessment of the level of risk, it is necessary to rank the severity and frequency of occurrence by level (Table 4). For each level of severity (for example, low impact), it is necessary to define a certain set of characteristics (for example, minor injury, bruise, etc.) and similarly determine the characteristics of the frequency of occurrence of the risk (for example, rarely occurs - once a year). In order for the level of risk to have a quantitative value, we assign a certain number of points to each level and obtain a certain number of points characterizing the level of risk.

Now that we have obtained the quantitative value of the level of each risk, it is necessary to rank them according to the levels highlighted in Table 4, for example:
- Minor risk (highlighted in white);
- Acceptable risk (highlighted in pink);
- Unacceptable risk (highlighted in red).
Each enterprise chooses the number of risk levels itself, depending on the scale and number of jobs with difficult (hazardous) working conditions. A certain number of points is assigned to each level and, based on this, a register of significant (unacceptable) risks of the enterprise is formed (Table 5).

Since the OHSAS 18001 standard requires the management of significant (unacceptable) risks, it is first necessary to create a separate register of significant (unacceptable) risks and develop management measures for them.
Stage 6. Development of risk management measures
to be continued...